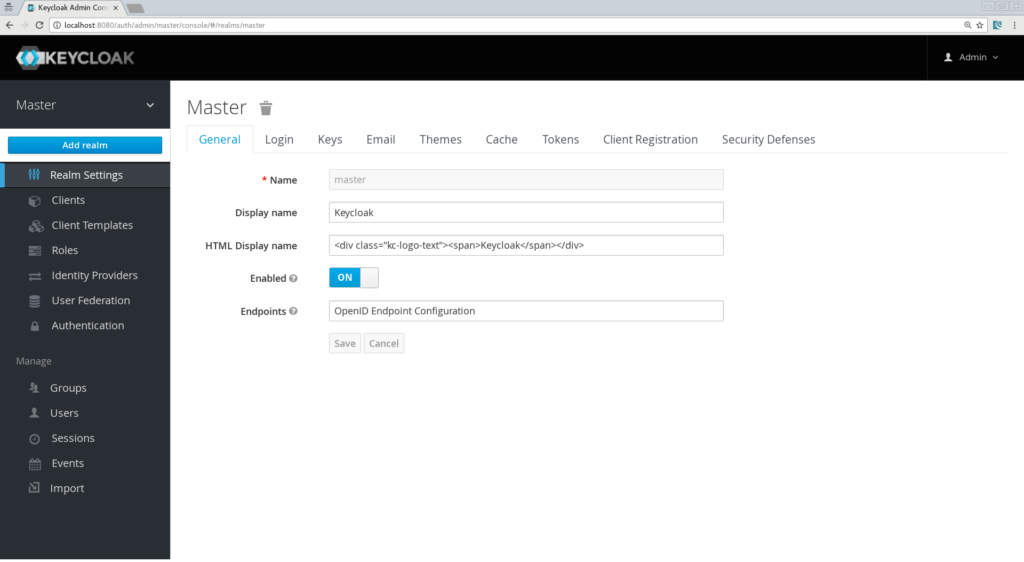
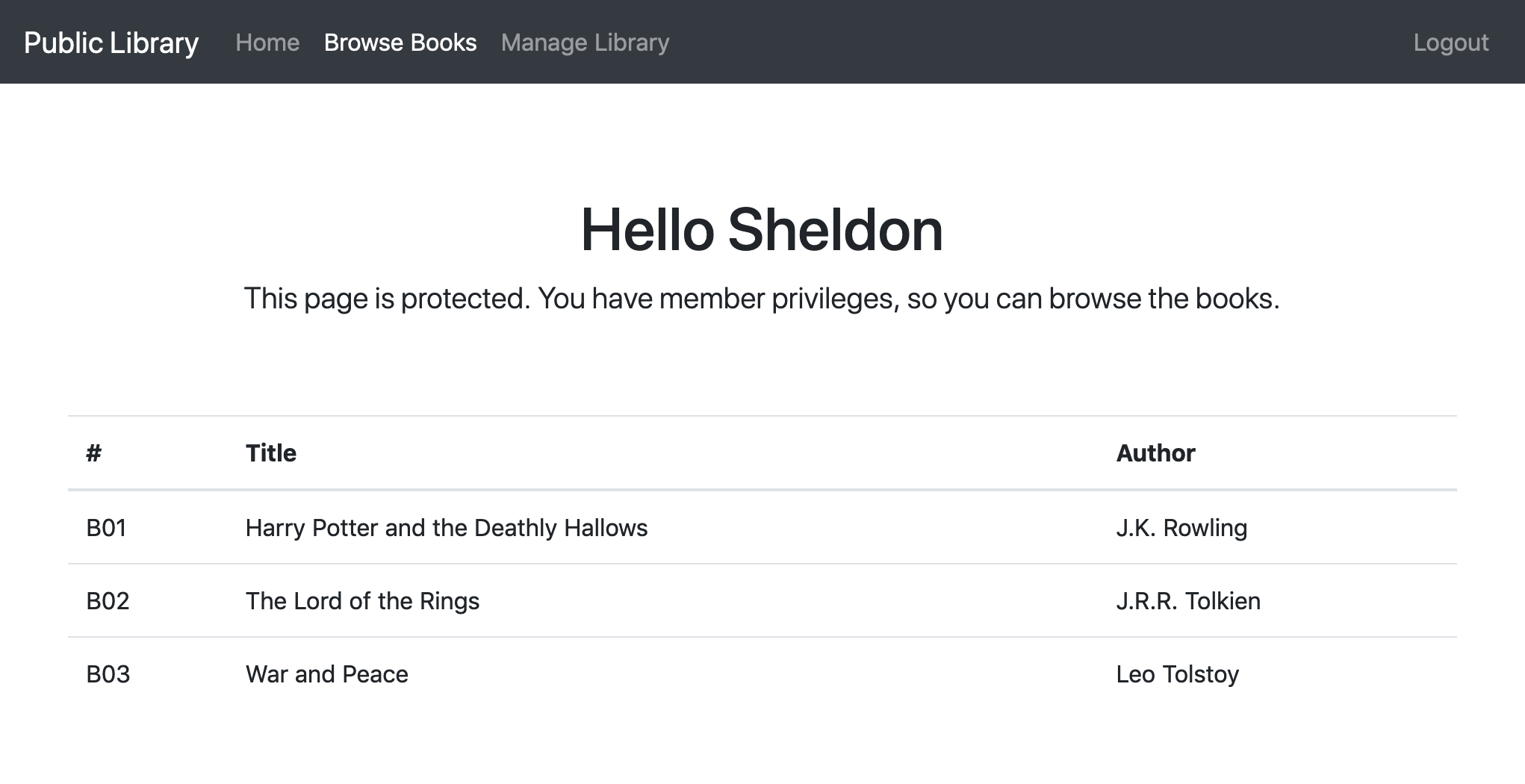
Securing your Spring Boot application with Spring Security and Keycloak | Michael Altenburger | Java enthusiast, Open-Source fanatic
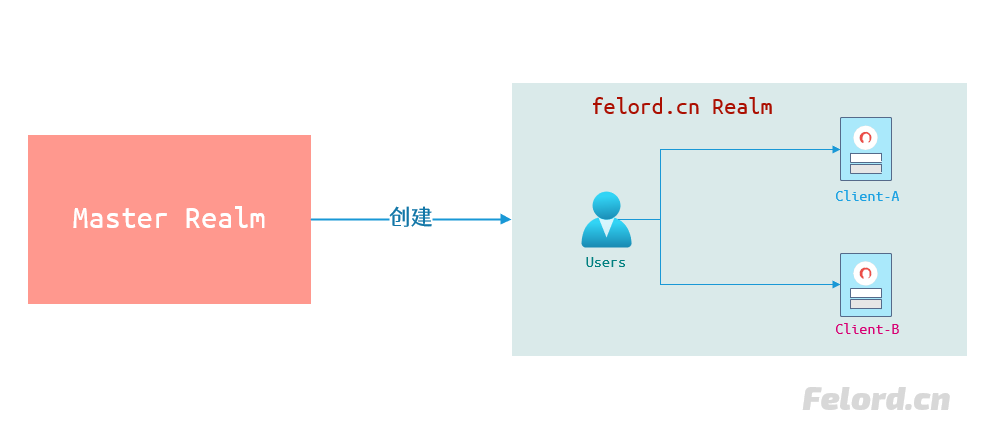
Protecting Your Spring Boot Applications with the Keycloak Authentication Authorization Platform - Spring Cloud






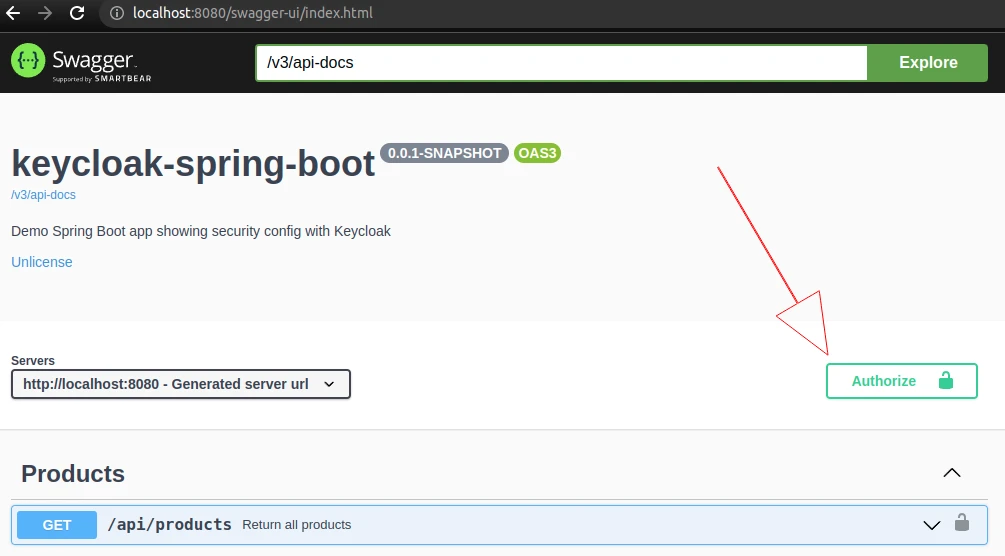

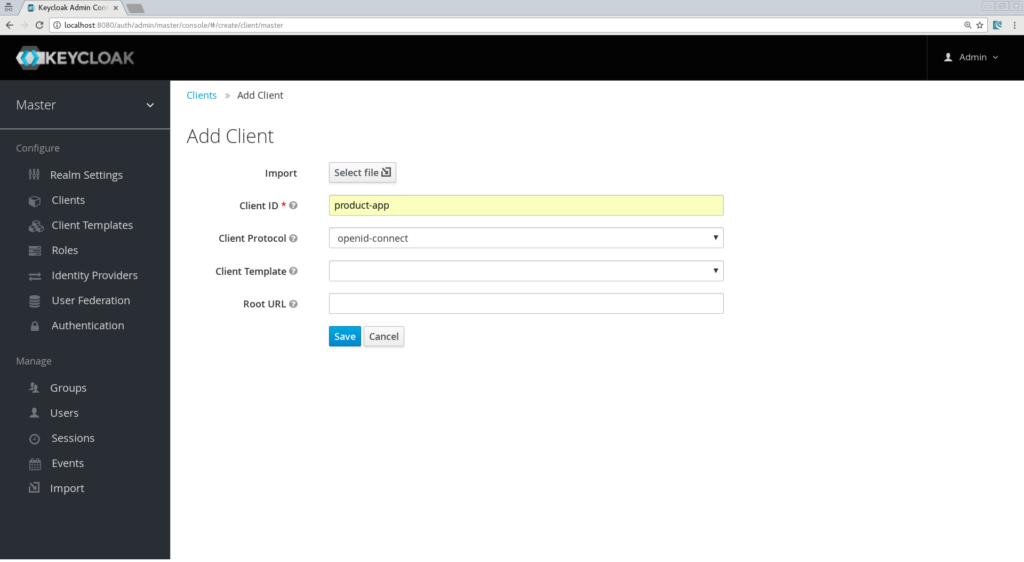
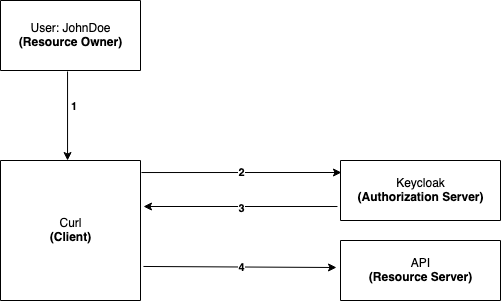





.png)