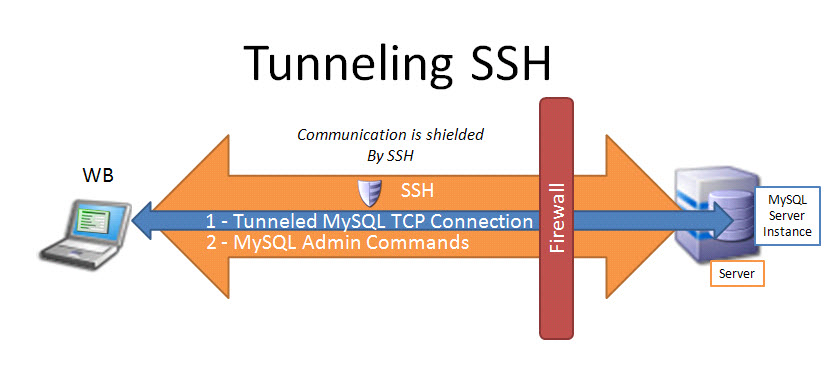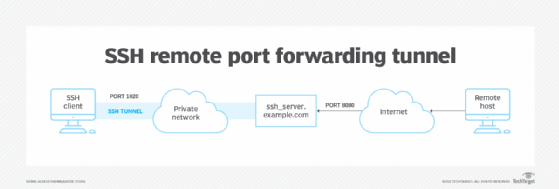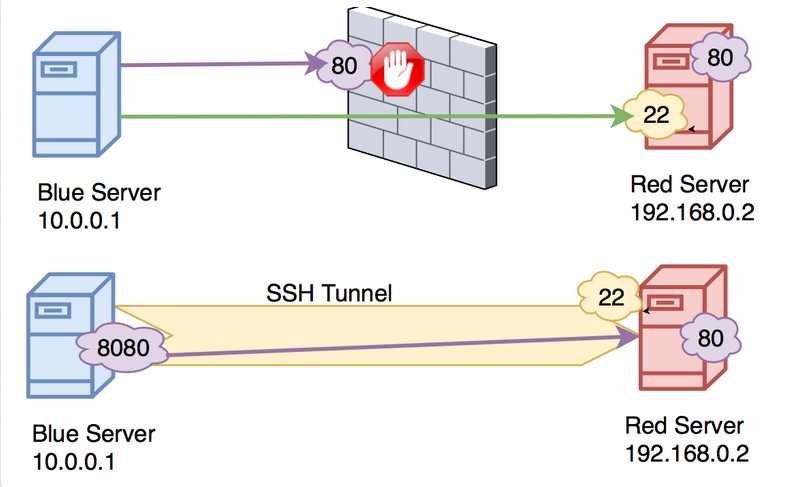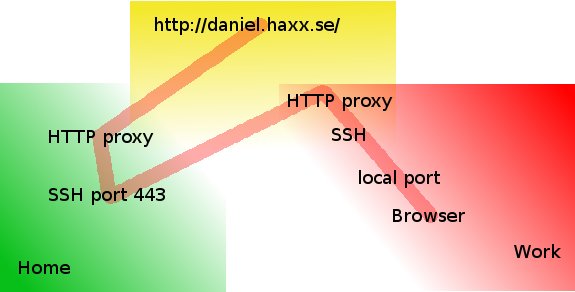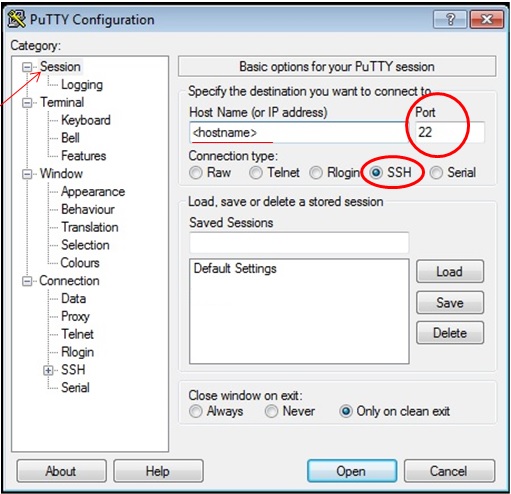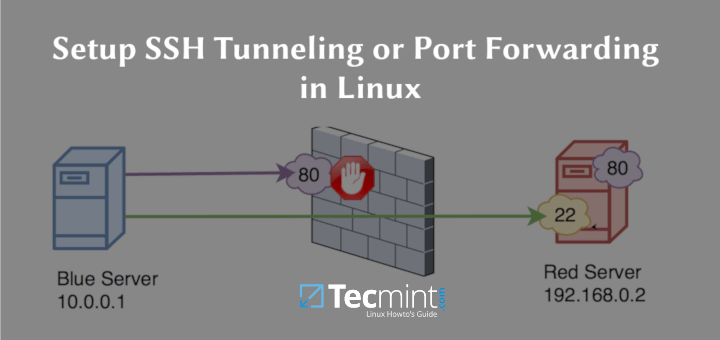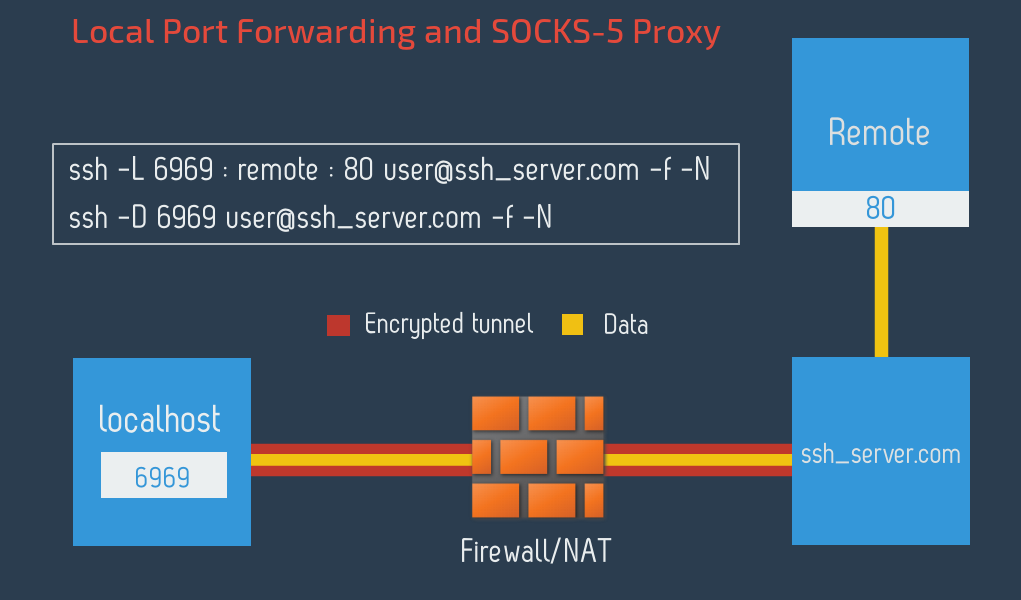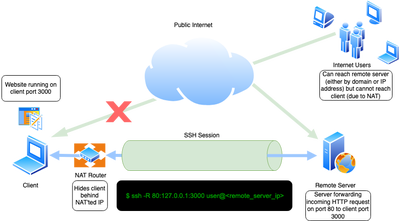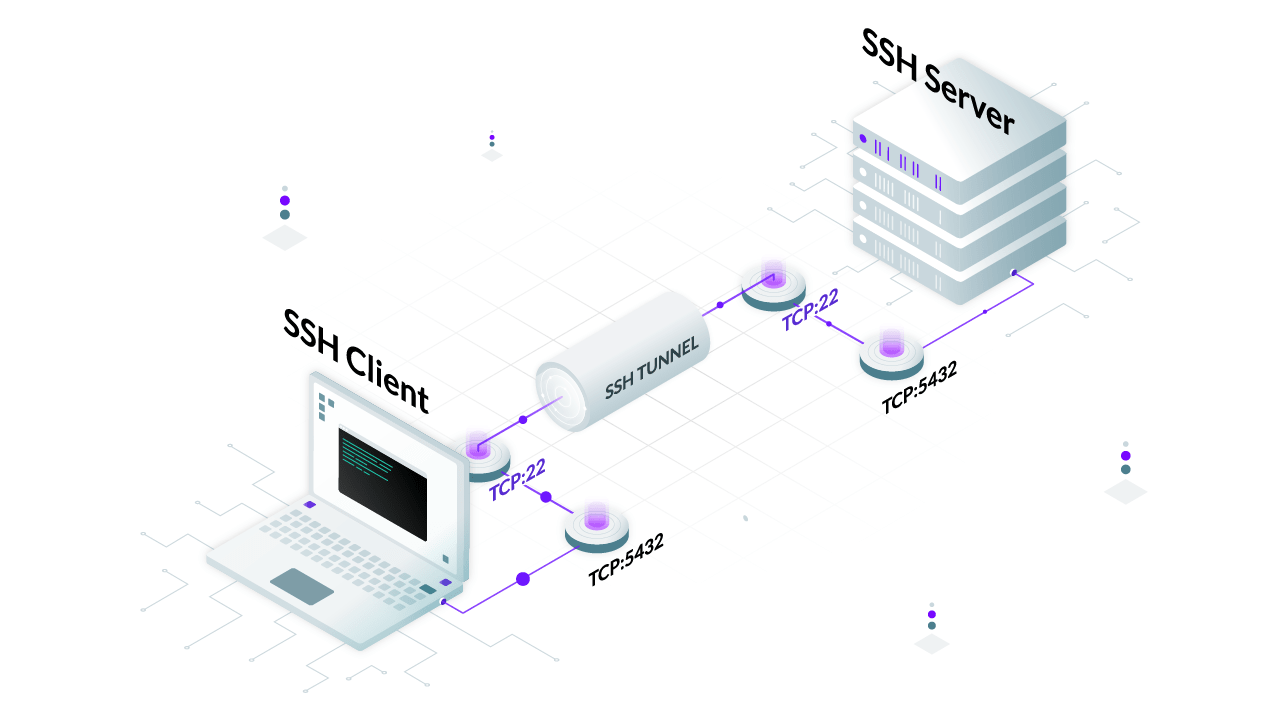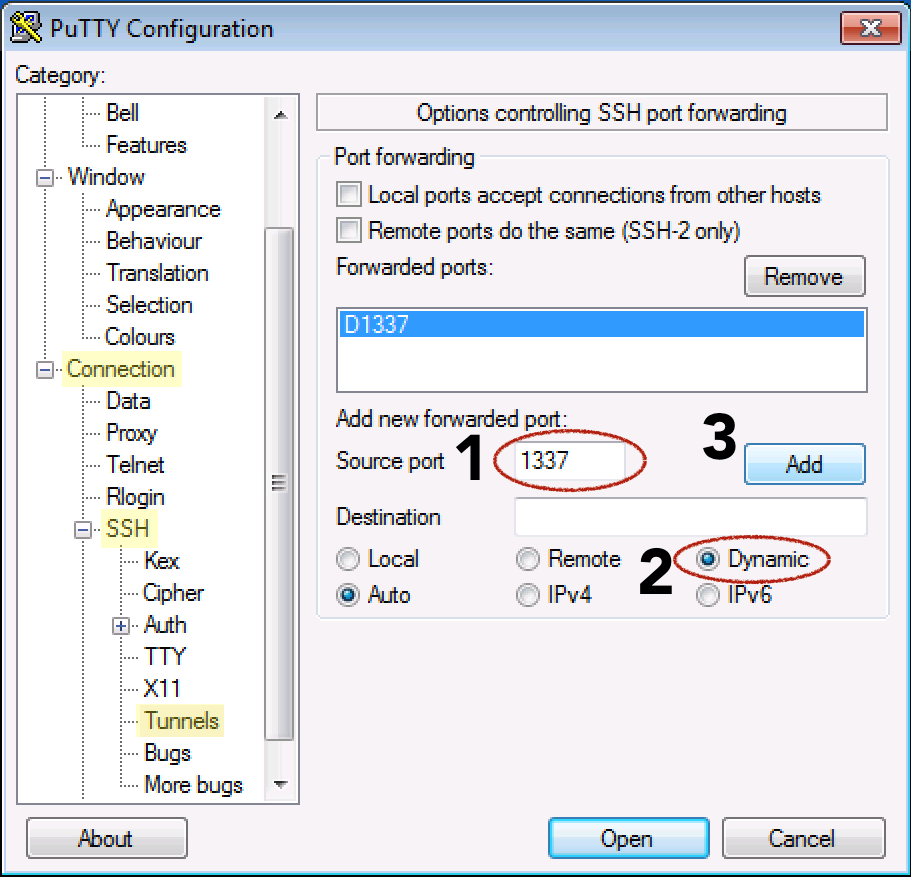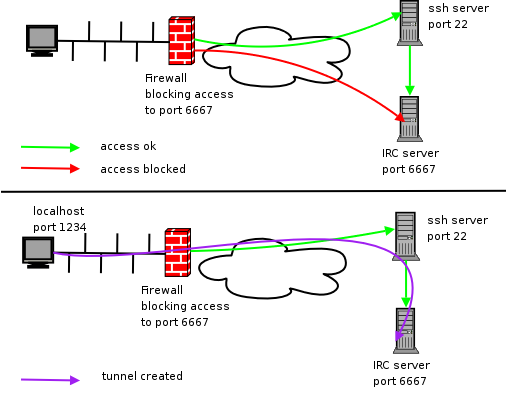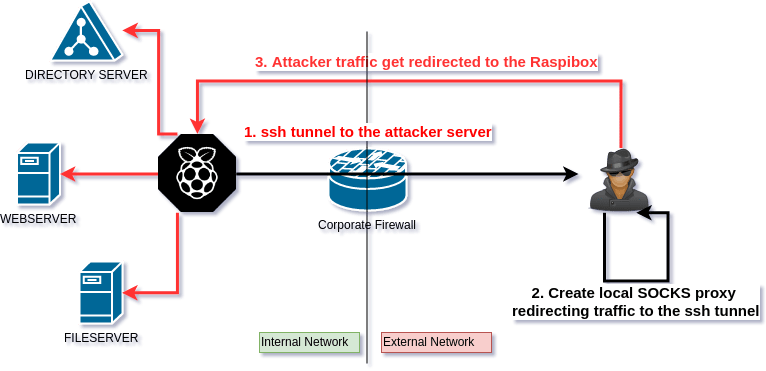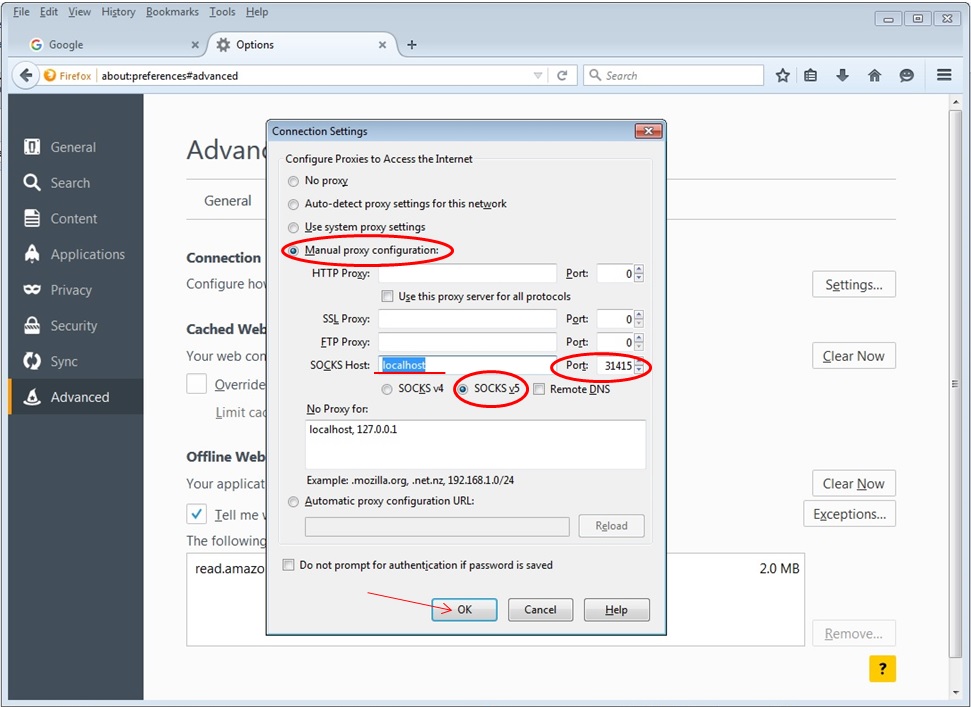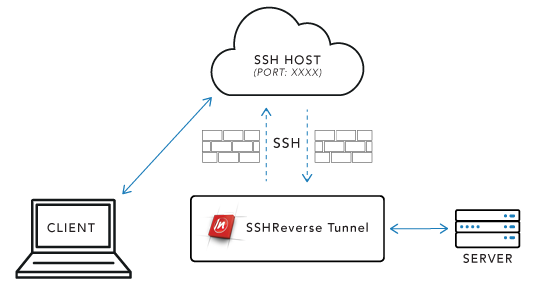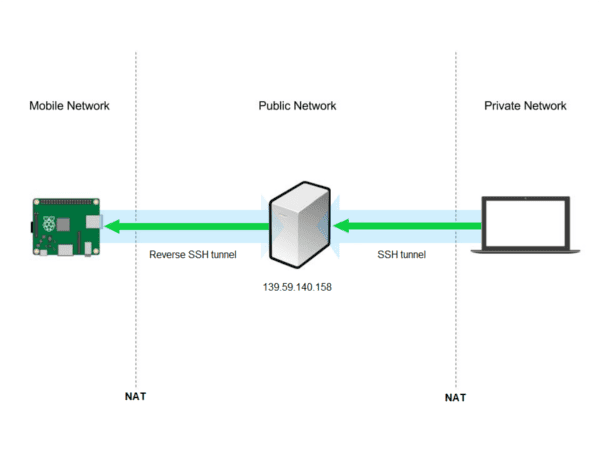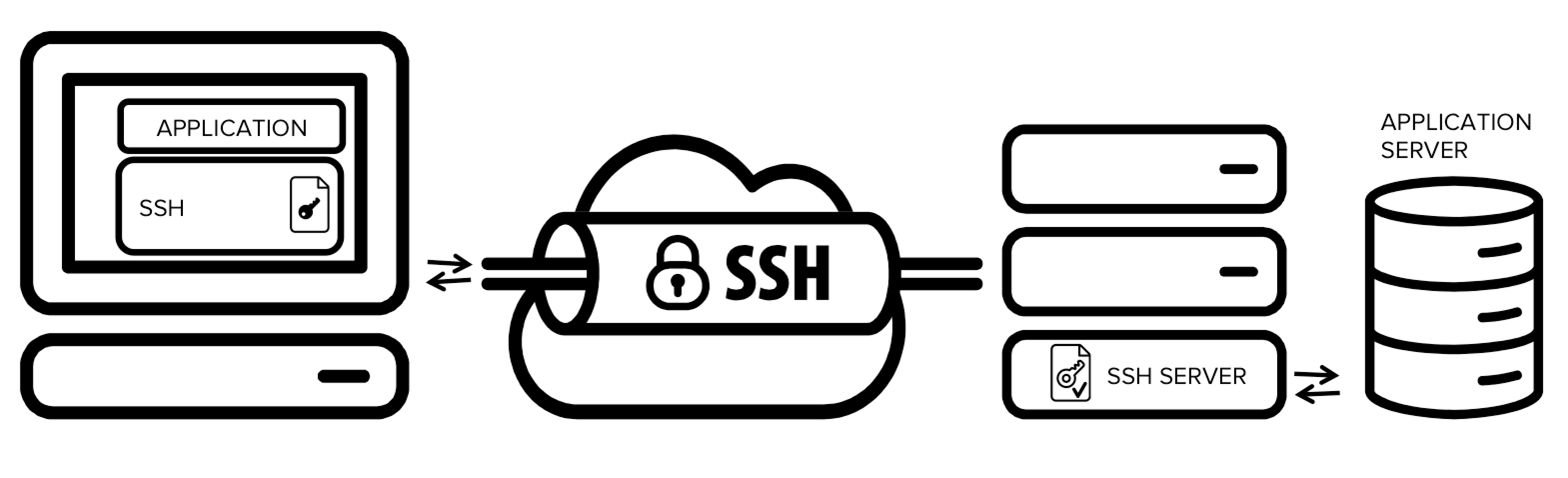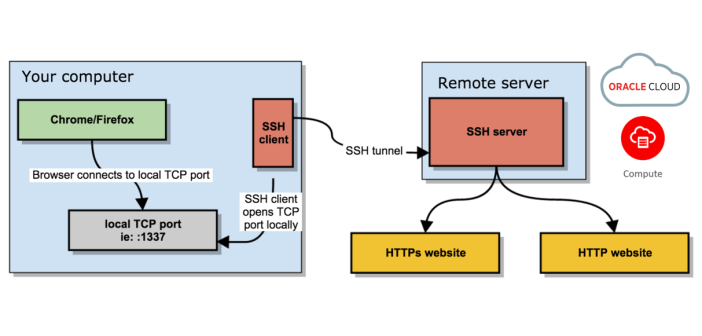
Secure browsing using a local SOCKS proxy server (on desktop or mobile) and an always free OCI compute instance as SSH server
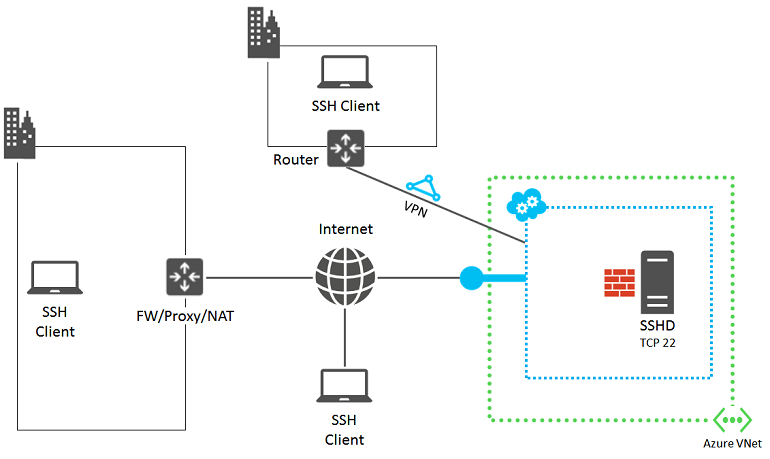
Risoluzione dettagliata dei problemi relativi a SSH per una macchina virtuale di Azure - Virtual Machines | Microsoft Learn

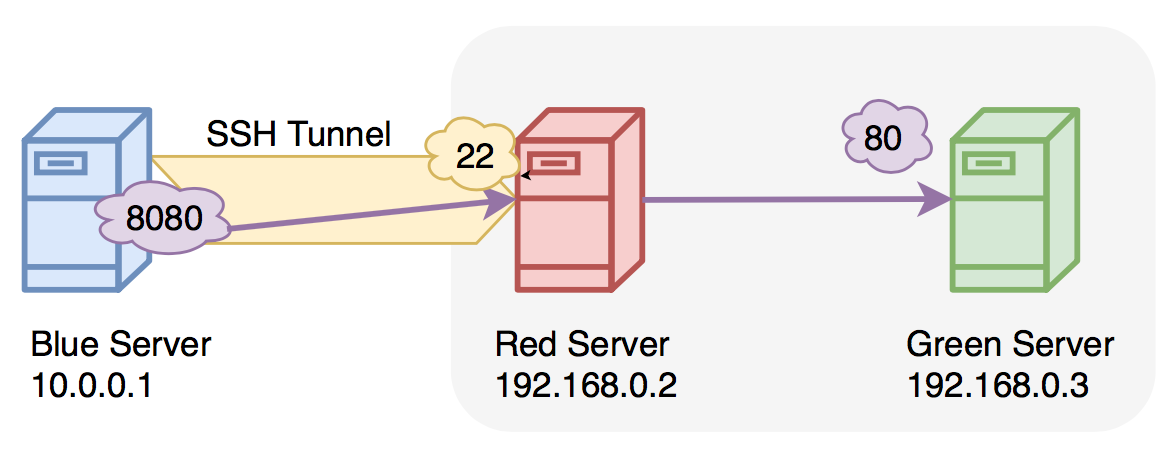
What's ssh port forwarding and what's the difference between ssh local and remote port forwarding - Unix & Linux Stack Exchange